Oslo-based Norma Cyber often knows when a shipping outfit has been attacked by cyber criminals even before the company’s security alarms sound.
It does so by accessing and monitoring covert criminal forums on the dark web, where all sorts of data is up for sale.
“We look for who they target, the infrastructure they use, and how they attack, and this, with our intelligence, gives us the opportunity to identify them,” said Svein Ringbakken, chair of the board at Norma Cyber.
The Norwegian Maritime Cyber Resilience Centre, known as Norma Cyber, is a joint venture between the Norwegian Shipowners’ Association and the owners’ mutual war risks insurance association, DNK.
All three share the same wood-panelled building on the Oslo waterfront, although Norma Cyber’s office space is chrome and glass with large curved monitors on the desks and an operation centre with huge flat screens showing vessel positions.
One of its services is to enable its members to share attack information discreetly with the wider market.
“They can report to us, and we can share the information and not tell anyone which company it is,” said Ringbakken. “No company would go out early in an incident and say anything about an attack.”
Clear message
His message is clear: suffering a cyber attack is sensitive and companies do not want to advertise a breach for fear of how it may impact clients and suppliers.
Norma Cyber has 140 members, mostly Norwegian shipowners, but more recently this has been expanding to include shipping companies from other countries and peripheral sectors.

Created to help shipping companies assess cyber threats, Norma Cyber has ways of probing the dark web and the forums used by criminals, to see when sensitive data may be up for sale.
There are two types of cyber-attackers, according to Ringbakken.
There are state actors, who work under the instructions of a country’s government involved in cyber sabotage. These are most likely attempting to create disruption for their target rather than elicit money from them.
Then there are the criminal actors, who are more opportunistic and seek money and have online communities where they share information.
“There are the access brokers who get inside a company’s system, then once they have broken in they sell the access to a gang capable of getting around inside a corporate network and setting the ransomware,” explained Ringbakken.
Infiltrating forums
Norma Cyber has infiltrated some dark web forums and can see when data or back-door access to a company is being auctioned.
“These are open forums,” Ringbakken added. “So you need to speak the language to sneak in.”
He was reluctant to reveal further details of how they infiltrate the dark web, but he added that they often know which criminal gangs are behind attacks.
“Most of the threats are not specific to maritime, but we have identified ones that have targeted maritime.”
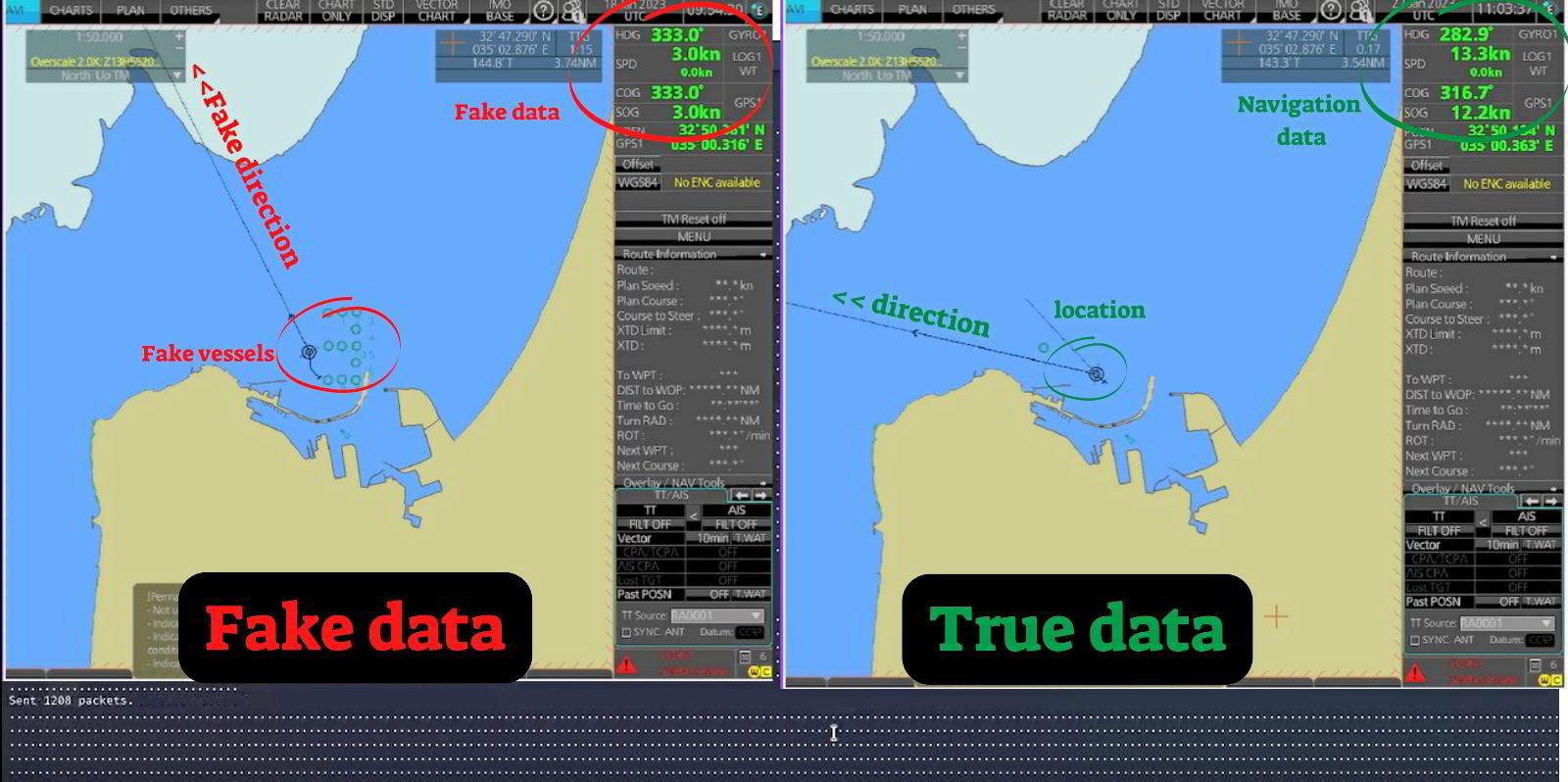
As nearly all attacks in the maritime domain are from criminal not state actors, the risks of a fleet-wide attack on shipping are extremely small.
‘Opportunistic’ attacks
Norma Cyber chief technology officer Oyvind Berget points out that cyber criminals are generally opportunistic, and will attack any system they can with ransomware, whether a dairy producer, a vehicle manufacturer, a port or a shipowner. So the attack will be on the shipowner’s office-based system rather than the vessels.
“Vessels do not have the same equipment on board and have different levels of connectivity, so it is not one common IT infrastructure,” Berget said.
But while it is more difficult, it is not a risk they are ignoring.
Norma Cyber has initiated the rollout of an additional service for shipowner members. This entails deploying a monitoring system to their vessels for installation on board. The system is designed to monitor data flows and promptly detect any anomalies.
It comes at an extra cost, but the laptop-sized device can be easily installed to give owners and operators of critical vessels additional peace of mind. Particularly, if they have vessels that European governments may consider part of the country’s transportation or energy infrastructure.
New rules to boost security
The European Union is tightening its cyber resilience and security regulations later this year. The NIS2 directive, an acronym for Network and Information Security, aims to increase resilience in key sectors, and transportation is one of them.
It puts a greater onus on the company to evaluate and control threats that its own suppliers and service providers may be opening up.
Shipowners within this need to find out from their governments if they fall under the directive’s requirements, warned Ringbakken.
“Under NIS1 regulations organisations would be told by their governments if they fell under NIS1, but in NIS2 it is up to the shipowner to know if they are in.”(Copyright)





